As a followup on my previous post about Internet content filtering, I thought it would be best to let you know that in order to better examine the filtering strategy taken by Internet-Rimon and NetSpark I arranged a remote session with a family member and used TeamViewer to remote control his computer. It took me less than an hour to gain access to any website without any filtering. In the following screenshot, on the left side you can see Internet-Rimon’s message saying that I tried to access a restricted website (888.com) and on the right side, the actual website that I have successfully accessed after bypassing the filtering mechanisms.
In the process of bypassing the filtering mechanism, I came across a security issue that, at least to me – was even more disturbing which is the way these services handle (and filter) encrypted traffic. In my opinion, this is even more dangerous than anything the user might see on a restricted website.
Here’s a description of this service as it appears on NetSpark’s website:
“When enabled, content is unencrypted for inspection and Quilting on NetSpark’s secure servers, and then re-encrypted and delivered securely under NetSpark’s SSL certificate to the end user. Full transparency to the status of the original SSL certificate status is maintained to ensure maximal credibility.”
This seems to be a reasonable process, to decrypt the traffic on the provider’s servers and then encrypt the traffic back. It seems only a technical issue that should concern only geeks like myself – right?
Actually – No. I think it should concern everyone that uses these services and I’ll explain why:
In order to better understand the danger that threatens all the users of such a filtering service we must first understand (to some degree) how this type of encryption actually works:
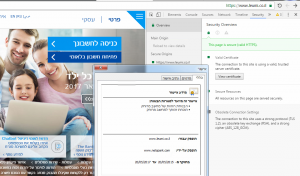
When we access a website that its address starts with “https://” and small green lock icon appears next to the website’s address (in chrome browsers) it means that our web browser will try to encrypt all the data that is being sent from the user’s computer to that website, but how can the user be sure that the website that he/she sees is actually the website that he/she was looking for? The answer is just two mouse clicks away… If we’ll click that green lock icon and then click on “View certificate” we can see who guarantees us that this website is the one that we think it is. Also, in that screen we can see additional detail regarding the security of the encryption process.
For example, let’s take one of the largest banks here in Israel: Leumi. If you’ll access that bank’s website at “https://www.leumi.co.il” you can see that the company that issued the certificate for that website (and by that guarantees us that this website is the one that we think it is) which is in this case Symantec and that this certificate is valid (until 20/5/2017). Also, on the right side we can see that the browser warns us that this communication uses an obsolete protocol (TLS 1.0) and a key length of 256 bits which is considered strong and on the other hand it uses an old hashing technique (it doesn’t really matter what it is now…):
Now that we know all these details we can wisely decide (based on the recommendations of our browser) if we would like to enter our personal details in this kind of website and not less important – we can see when these details about the website change. For example – if the company that supplied the certificate changes or the security of the connection changed. Some of the web browsers can detect such changes automatically and alert you when they happen.
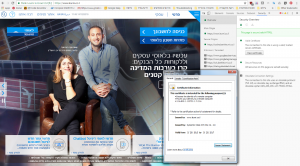
So, how is that different for people that use Internet Rimon’s and NetSpark internet filtering services? This is how that same bank’s web page looks like when I accessed it via Internet-Rimon:
Looks the same… – but God is in the details.
As you can see in EVERY encrypted website the organization that supplied the certificate is always the same: always NetSpark and always it’s security level is the same. The meaning of all this is that not the user nor his/her browser can technologically or otherwise determine the actual identity of the website that you just tried to access. In the era that one of the most common attack types is Phishing attack (in which the user is presented with a website similar to the attacked website, claiming to be it) I think that this creates a huge security risk for those users. After all – If you surfed to a website that you thought to be Facebook and uploaded photos of you and your family and then discovered that it wasn’t Facebook at all but a website that was created by criminals, wouldn’t you think that this it a severe risk? I sure would.
Also, it is important to understand that ALL of the traffic to and from all the encrypted websites is being decrypted on the filtering service’s servers and so if (and I’m not saying that it is but who knows really…) if at some point a hacker will get access to these servers such a hacker will have access to data that he/she could never access anywhere on the planet: credit-cards, bank accounts, personal details, health information, passwords – actually: EVERYTHING…
It is important to know that nowadays, security experts mostly agree that the next security breach is not a matter of “if” but “when” and “will we know that it happened”. With that in mind maybe it will be better to ask yourself again: What do we gain by using such a service and what do we lose?


Yup. Unfortunately correct. You are basically handing the keys to all your internet secrets over to Netspark and their focus is on protecting your kids – not your credit cards.
Just learning about TLS certs and came to this realization :0
Any suggestions as to a better filtering solution…?